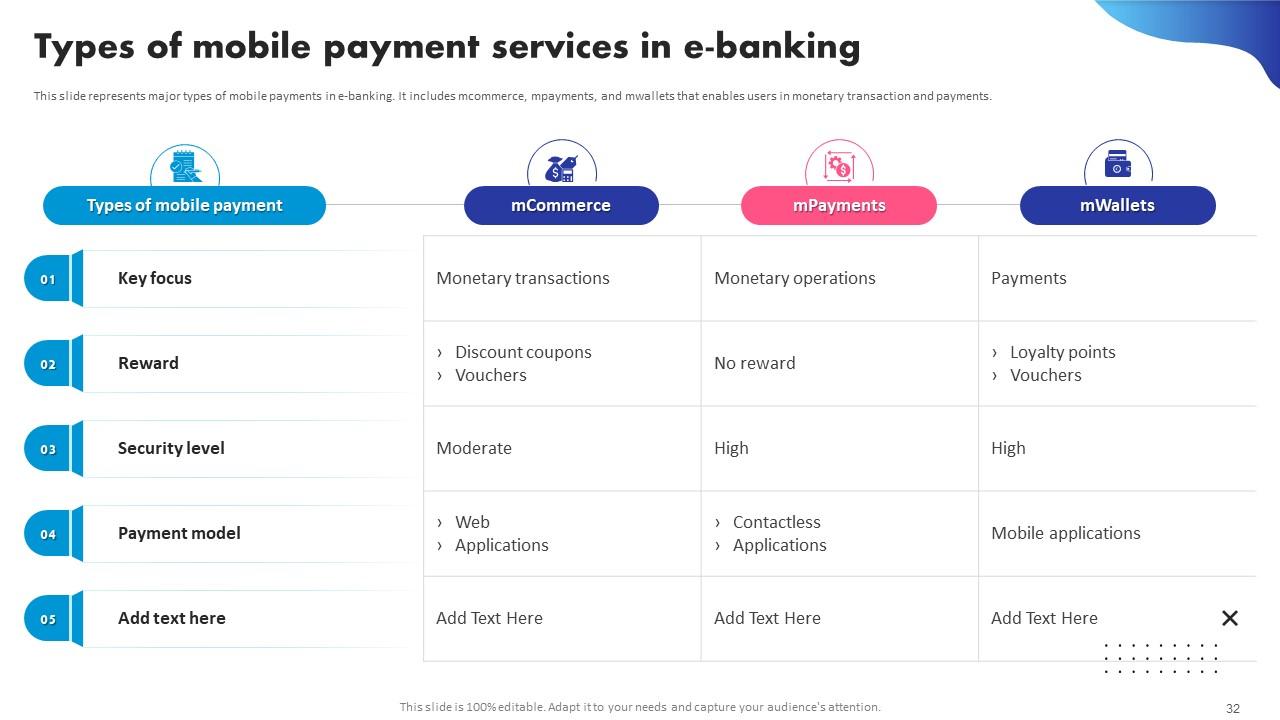
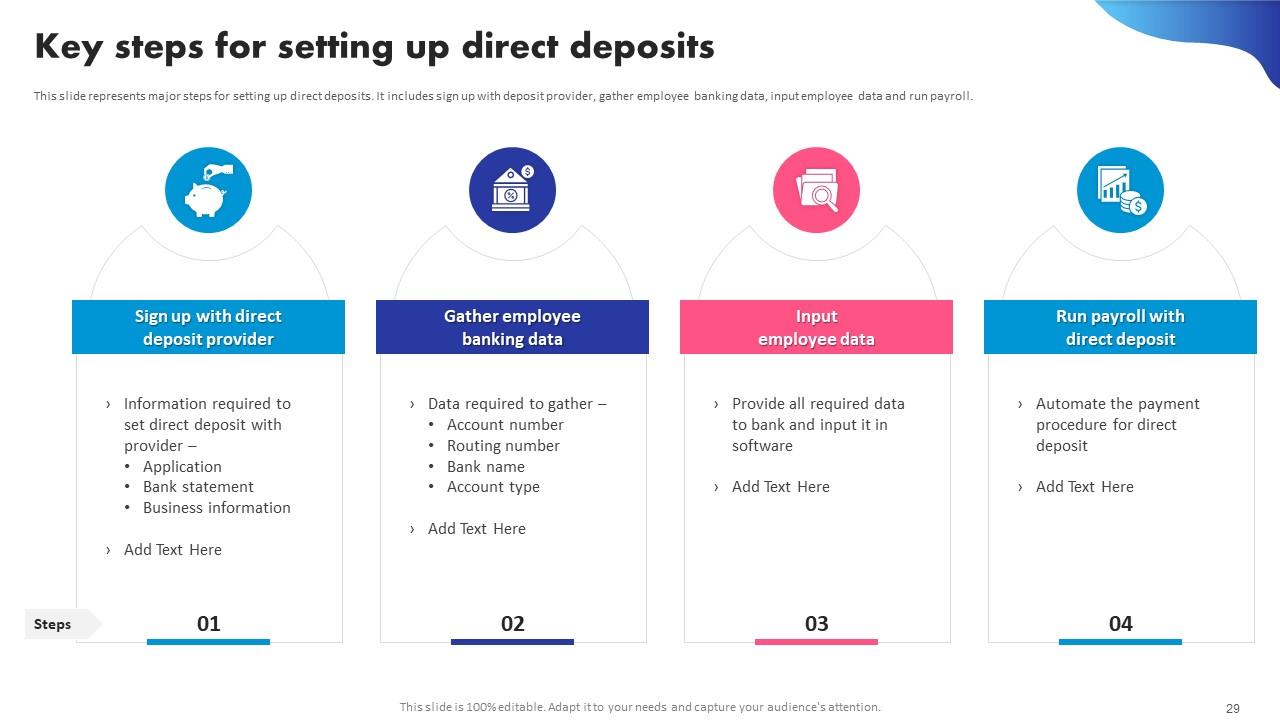
All Categories
Featured
Table of Contents
Suppliers that uncover the vulnerability might create spots or encourage workarounds to alleviate it though individuals require to deploy that reduction to remove the susceptability in their systems. Zero-day attacks are serious hazards. Prospective attack vectors for a zero-day vulnerability are similar to known susceptabilities and those that have available patches. Therefore the formula for the size of the home window of susceptability is: t2 t1b. Keep in mind that t0 is not the exact same as day absolutely no.
For regular vulnerabilities, t1b > t1a. This indicates that the software application vendor knew the vulnerability and had time to publish a safety and security patch (t1a) before any type of hacker can craft a practical exploit (t1b). For zero-day exploits, t1b t1a, such that the manipulate becomes energetic before a patch is made available.
It has been recommended that an option of this kind might run out reach because it is algorithmically impossible in the general case to assess any kind of arbitrary code to establish if it is harmful: therefore an analysis lowers to the stopping issue over a straight bounded automaton, which is unsolvable.
Security Consultants - The Facts
Most modern-day antivirus software program still uses trademarks but also accomplishes other sorts of evaluation. [] In code evaluation, the machine code of the data is evaluated to see if there is anything that looks dubious. Commonly, malware has characteristic practices; code evaluation tries to identify if this is existing in the code.
It is not constantly easy to establish what a section of code is planned to do, specifically if it is extremely complicated and has actually been deliberately written with the intent of defeating evaluation. Another limitation of code analysis is the moment and sources readily available. In the affordable world of anti-virus software program, there is constantly an equilibrium between the performance of analysis and the time delay involved.
This can be orders of magnitude quicker than assessing the same code, yet have to withstand (and spot) attempts by the code to find the sandbox. Common signatures are signatures that specify to certain behavior instead of a certain item of malware. A lot of new malware is not totally unique, yet is a variation on earlier malware, or consists of code from one or even more earlier instances of malware.
Fascination About Banking Security
Held in a protected and durable cloud atmosphere, Our advanced, scalable solutions are designed to accelerate innovation and aid banks deliver the experiences users demand currently and in the future. We provide public and private hybrid cloud holding solutions, with releases both in our own fully repetitive and very readily available information facilities based in the United States, also on the AWS public cloud, operating 24 hr a day, 365 days a year, under the most extensive high quality and security criteria.
The cash conversion cycle (CCC), also called the web operating cycle or cash money cycle, is a statistics that shares, in days, the length of time it takes a company to convert the cash invested in stock back right into money from selling its service or product. The much shorter the money cycle, the better, as it shows less time that cash is bound in receivables or inventory.
This statistics considers just how much time the firm needs to offer its supply, just how much time it requires to gather receivables, and just how much time it needs to pay its costs. The CCC is just one of numerous quantitative procedures that aid evaluate the performance of a company's operations and administration.
What Does Banking Security Do?
One need to remember that CCC applies just to pick markets depending on supply administration and related procedures. The cash conversion cycle (CCC) is a metric that expresses the length of time (in days) that it considers a business to transform its financial investments in inventory and various other sources into capital from sales.
g., year = 365 days, quarter = 90) The first stage concentrates on the existing supply degree and stands for the length of time it will take for the organization to market its stock. This number is calculated by using the days inventory outstanding (DIO). A reduced worth of DIO is favored, as it shows that the business is making sales rapidly, implying better turnover for business.
Stock=21(BI+EI)BI=Starting inventory, EI=Ending stock The second phase concentrates on the existing sales and represents for how long it requires to accumulate the money produced from the sales. This number is computed by using the days sales outstanding (DSO), which separates typical balance dues by profits daily. A reduced value is chosen for DSO, which indicates that the firm has the ability to gather capital in a brief time, consequently boosting its money position.
The 25-Second Trick For Security Consultants
Accounts Receivable=21(BAR+EAR)BAR=Start AREAR=Ending AR The third stage concentrates on the existing impressive payable for business. It considers the amount of cash that the firm owes its current vendors for the stock and products it acquisitions, and it stands for the period in which the firm must repay those obligations.
Increasing sales of stock for profit is the primary method for an organization to make even more profits. However how does one sell much more things? If money is easily offered at regular intervals, then one can produce even more sales commercial, as regular accessibility of funding results in a lot more items to make and sell.
A firm can also sell items on credit rating, which results in balance dues (AR). Therefore, cash money isn't a variable till the business pays the accounts payable and collects the receivables. Timing is thus a vital aspect of cash money monitoring. CCC traces the life cycle of cash made use of for service activity.
The 9-Minute Rule for Security Consultants
CCC may not provide meaningful reasonings as a stand-alone number for a given period. Analysts use it to track a business over numerous amount of time and to compare the firm to its rivals. Tracking a firm's CCC over multiple quarters will show if it is boosting, keeping, or worsening its functional efficiency.
Latest Posts
Plumbing in Raleigh
24/7 Plumbing servicing Raleigh, Texas
24/7 Plumbing in Raleigh