All Categories
Featured
Table of Contents
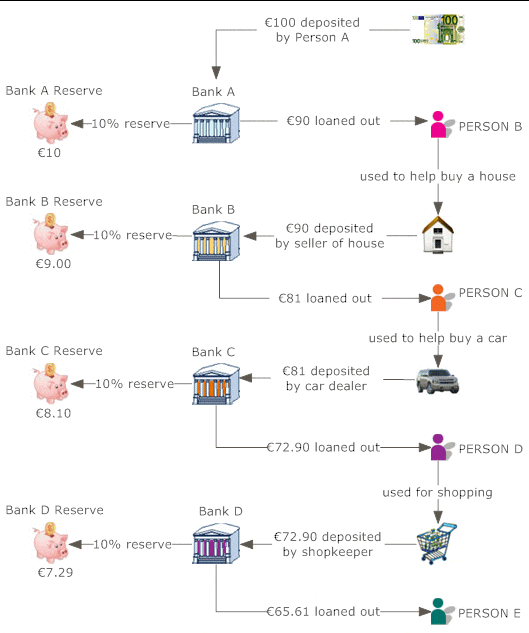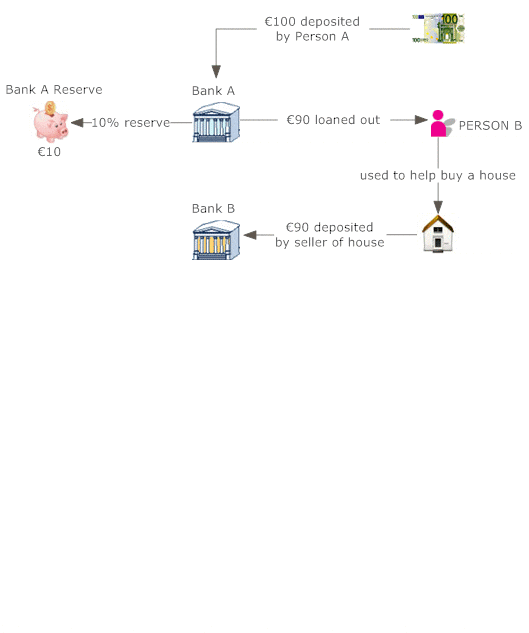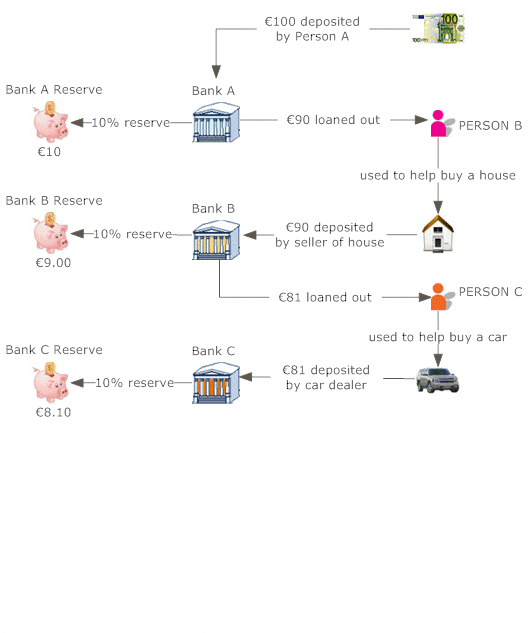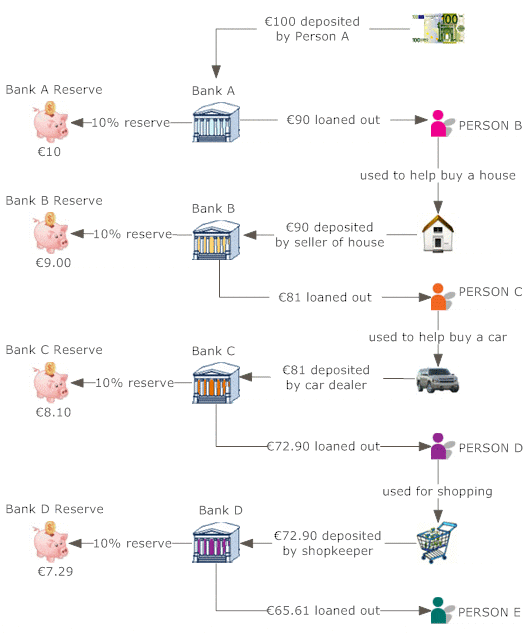
The cash conversion cycle (CCC) is just one of several procedures of management effectiveness. It gauges exactly how quickly a business can transform cash available right into even more cash money on hand. The CCC does this by following the cash, or the capital financial investment, as it is initial transformed into inventory and accounts payable (AP), with sales and receivables (AR), and after that back right into cash.
A is the usage of a zero-day exploit to cause damages to or take data from a system influenced by a vulnerability. Software typically has safety and security vulnerabilities that cyberpunks can make use of to cause chaos. Software application designers are constantly looking out for susceptabilities to "spot" that is, establish a remedy that they launch in a new upgrade.
While the susceptability is still open, enemies can compose and implement a code to take benefit of it. As soon as assaulters recognize a zero-day vulnerability, they require a means of reaching the at risk system.
What Does Banking Security Mean?
Safety vulnerabilities are typically not found straight away. In current years, cyberpunks have been faster at exploiting vulnerabilities quickly after exploration.
For instance: hackers whose motivation is usually financial gain hackers encouraged by a political or social reason that desire the attacks to be noticeable to accentuate their cause cyberpunks that snoop on firms to obtain information concerning them nations or political stars snooping on or attacking another country's cyberinfrastructure A zero-day hack can exploit vulnerabilities in a range of systems, including: Therefore, there is a wide series of possible targets: People that utilize a prone system, such as a browser or running system Hackers can make use of protection vulnerabilities to compromise devices and build large botnets People with access to beneficial company information, such as copyright Hardware tools, firmware, and the Web of Things Large services and companies Government agencies Political targets and/or nationwide safety and security hazards It's practical to assume in regards to targeted versus non-targeted zero-day strikes: Targeted zero-day attacks are performed versus possibly valuable targets such as huge organizations, federal government companies, or prominent people.
This site uses cookies to help personalise web content, customize your experience and to maintain you visited if you register. By continuing to utilize this site, you are consenting to our use cookies.
Getting My Banking Security To Work
Sixty days later is generally when an evidence of idea emerges and by 120 days later on, the vulnerability will be included in automated vulnerability and exploitation devices.
Prior to that, I was just a UNIX admin. I was thinking of this inquiry a great deal, and what happened to me is that I don't recognize way too many individuals in infosec that picked infosec as a job. The majority of the people who I recognize in this area really did not go to university to be infosec pros, it just sort of happened.
You might have seen that the last 2 professionals I asked had somewhat various opinions on this question, but how crucial is it that somebody curious about this area know how to code? It's challenging to offer strong guidance without knowing even more regarding a person. Are they interested in network security or application safety and security? You can obtain by in IDS and firewall software globe and system patching without understanding any type of code; it's fairly automated stuff from the product side.
Examine This Report about Banking Security
With equipment, it's a lot various from the work you do with software safety and security. Would you say hands-on experience is extra crucial that formal safety education and certifications?
There are some, however we're possibly chatting in the hundreds. I assume the universities are recently within the last 3-5 years getting masters in computer system safety sciences off the ground. There are not a lot of students in them. What do you assume is the most important certification to be effective in the security area, despite a person's background and experience degree? The ones that can code generally [fare] much better.
And if you can understand code, you have a much better possibility of having the ability to comprehend how to scale your service. On the protection side, we're out-manned and outgunned continuously. It's "us" versus "them," and I don't understand the amount of of "them," there are, yet there's mosting likely to be too few of "us "whatsoever times.
The Ultimate Guide To Banking Security
For instance, you can picture Facebook, I'm not exactly sure several security people they have, butit's going to be a tiny fraction of a percent of their customer base, so they're mosting likely to need to determine exactly how to scale their services so they can safeguard all those customers.
The researchers observed that without understanding a card number in advance, an enemy can launch a Boolean-based SQL injection via this field. The data source responded with a five 2nd hold-up when Boolean true statements (such as' or '1'='1) were provided, resulting in a time-based SQL injection vector. An opponent can use this technique to brute-force query the database, permitting info from accessible tables to be exposed.
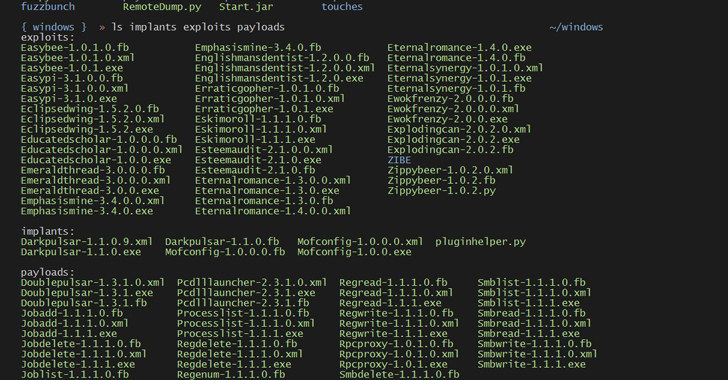
While the details on this dental implant are scarce presently, Odd, Work services Windows Web server 2003 Business as much as Windows XP Professional. Some of the Windows ventures were also undetectable on on-line documents scanning service Virus, Total, Safety And Security Architect Kevin Beaumont confirmed by means of Twitter, which suggests that the tools have actually not been seen before.
Latest Posts
Plumbing in Raleigh
24/7 Plumbing servicing Raleigh, Texas
24/7 Plumbing in Raleigh